Overview
The permission system provides fine-grained access control across different resources in your organization. It's built around three main concepts:
- Companies: The top-level organization unit
- Teams: Collections of resources that can be managed together
- Users: Individual members with specific permissions
Role feature
When creating a role, you can define permissions for each of the resources available in the platform :
-
Datasources
- Create, read, update, and delete datasources
- Query datasources for information
-
Users
- List user accounts within your company
- Edit user (which allow setting its teams and role)
Note Users can always read and update their own information
-
Teams
- Create and manage groups of resources
- Organize permissions and access control
-
Roles
- Allow to create, edit and delete roles
-
Content & Workflows
- Create, update, read and delete contents or workflows
-
Statistics
- Access the application
- Export result from the app into CSV file
-
Billing
- Allow to access billing menu
-
Companies
- View and update company information
- Not used right now
Teams feature
Teams organize users and resources in a hierarchical structure. Child teams automatically inherit access from parent teams, so you assign users once to the most specific team. The system handles broader access automatically.
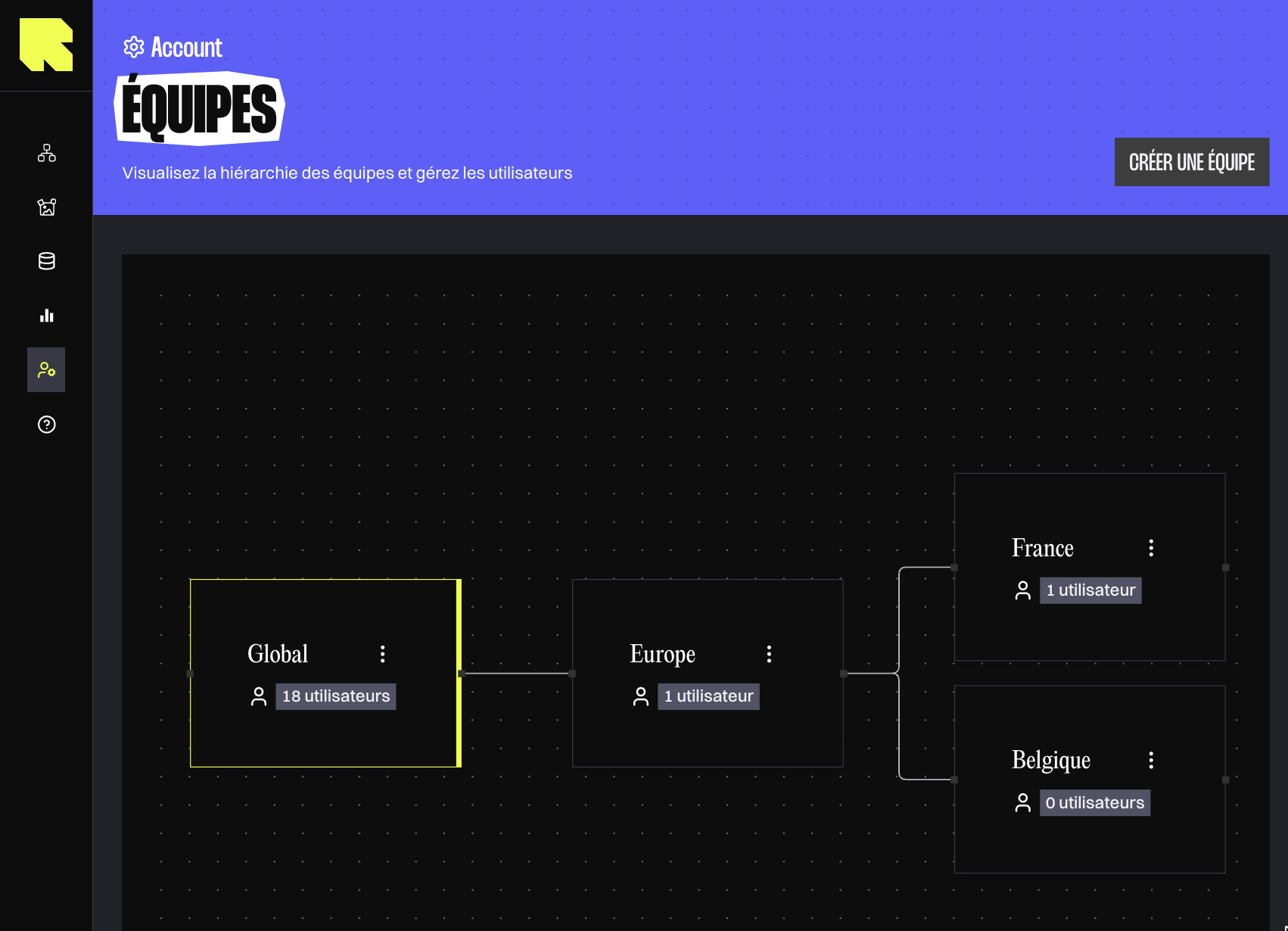
A team is a container for users and resources like datasources or workflows. Teams can have parent teams above and child teams below, creating a hierarchical structure. The system maintains relationships automatically when you create parent-child connections.
When you assign a user to a team, they automatically gain access to all descendant teams under it. If the "Exclude from Ancestor Inheritance" flag is enabled (which is not the case by default), that user will also gain access to all resources in ancestors teams.
Example: If "Engineering" contains "Backend Team" and you assign a user to "Backend Team," that user automatically gain access to resources in "Backend Team", and "Engineering" resources if the "Exclude from Ancestor Inheritance" flag is disabled.
Provide a descriptive name when creating a team. The system assigns a unique identifier and links it to your company. New teams start with no relationships; add them later.
Important: The system prevents circular references. Team A cannot be a parent of Team B if Team B is already a parent of Team A.
Every user must be assigned to at least one team. Assign users to the most specific team that matches their role. The system automatically associates them with all ancestor teams through inheritance.
Warning: Don't assign users to both a parent and its child team. The child assignment already provides child team access through inheritance.
You can edit team names, parent or child relationships, and inheritance settings at any time. Name changes apply immediately across the system.
Warning: You can delete teams, but the system enforces requirements to prevent data loss. Before deleting, the team must have no child teams nor resources (like workflows or contents) assigned. Delete or reassign children first.
